Embedded Ajax Brute-Force Tool
There are a few cases when preparing a PoC for brute-force attack on the login page can be complicated. It is no longer uncommon to find a login form based on web sockets, or which implements some sort of client-side encryption with JavaScript. In these cases, configuring a brute-attack quickly with a middle proxy (e.g. Burp’s Intruder) is not possible. It also happens that clients request for the penetration testings to be conducted on a specific machine, without access to common attacking tools.
For these reasons, I wrote a very minimalistic brute-force tool that runs inside the browser (the source code, following this post, has to be copy-pasted into browser’s JavaScript console).
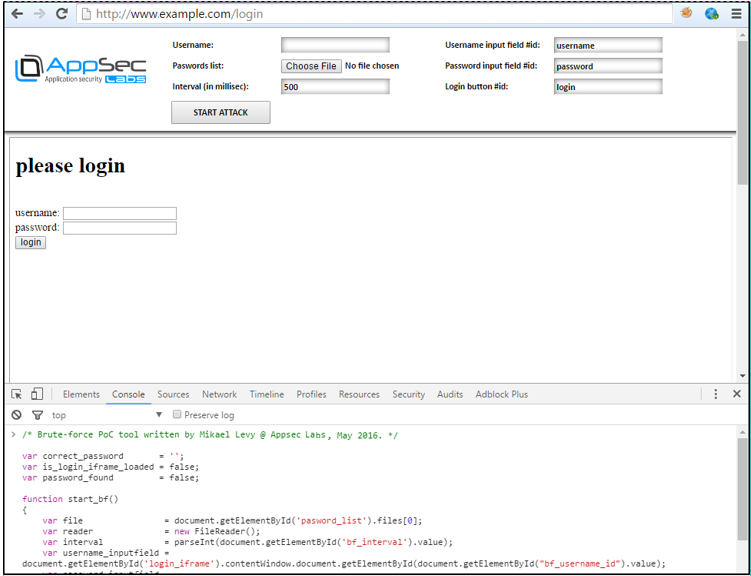
As it is possible to see in the following screenshot, a number of things need to be configured:
- The username on which we want to perform the guessing attack
- A password dictionary used for the attack (passwords are separated by new lines in the file)
- Interval: time (in milliseconds) between each attempt. Remember that we are simulating the brute-force inside the browser itself. It is almost as if the user is manually performing the attack, typing on his keyboard at an insane speed. Since the attack is single-threaded, it is important to wait for the response before making the next attempt.
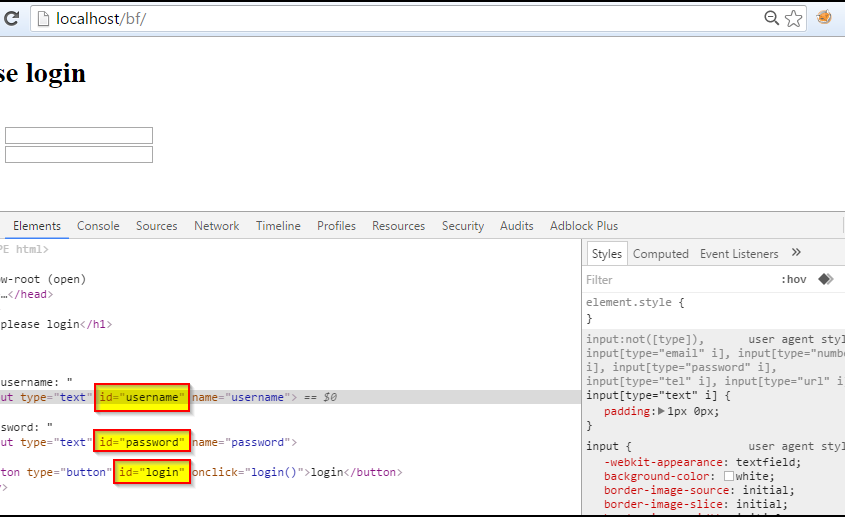
- In addition, the HTML IDs have to me manually extracted from the page’s HTML source code:
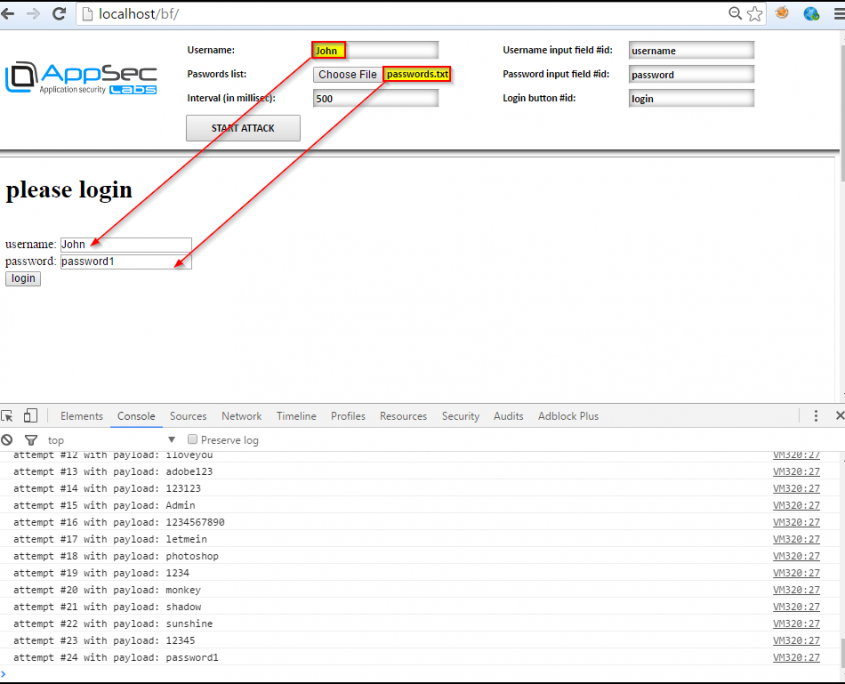
Finally, when the “START ATTACK” button is clicked, we can see the attack happening in real time on the page, while attempts are logged in the console:
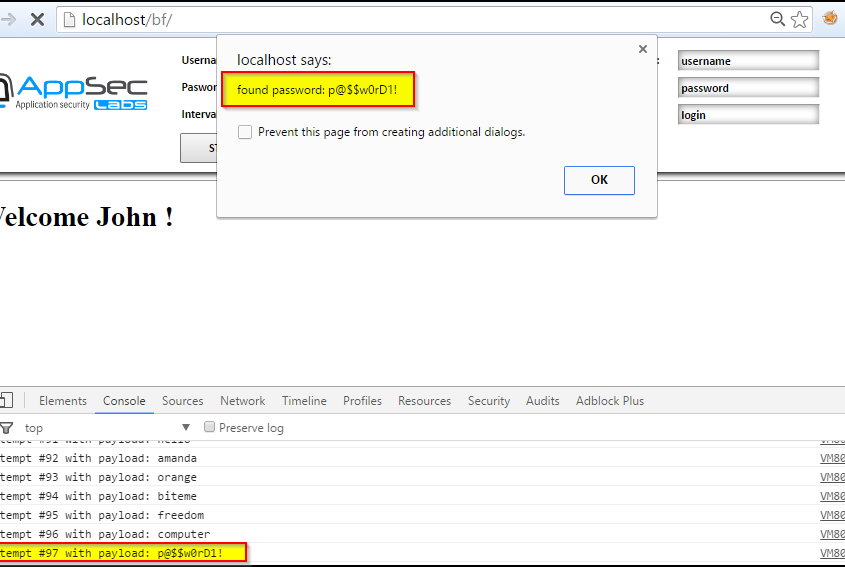
When a successful attempt is made, the last payload is displayed in an alert box:
Please note this tool only works on AJAX-like login forms, which do not redirect/refresh the page between each login attempt, but only display a failure message to the user.
Download the following source code, from here: bf.js



I can’t reach the site, I want to download the js file.