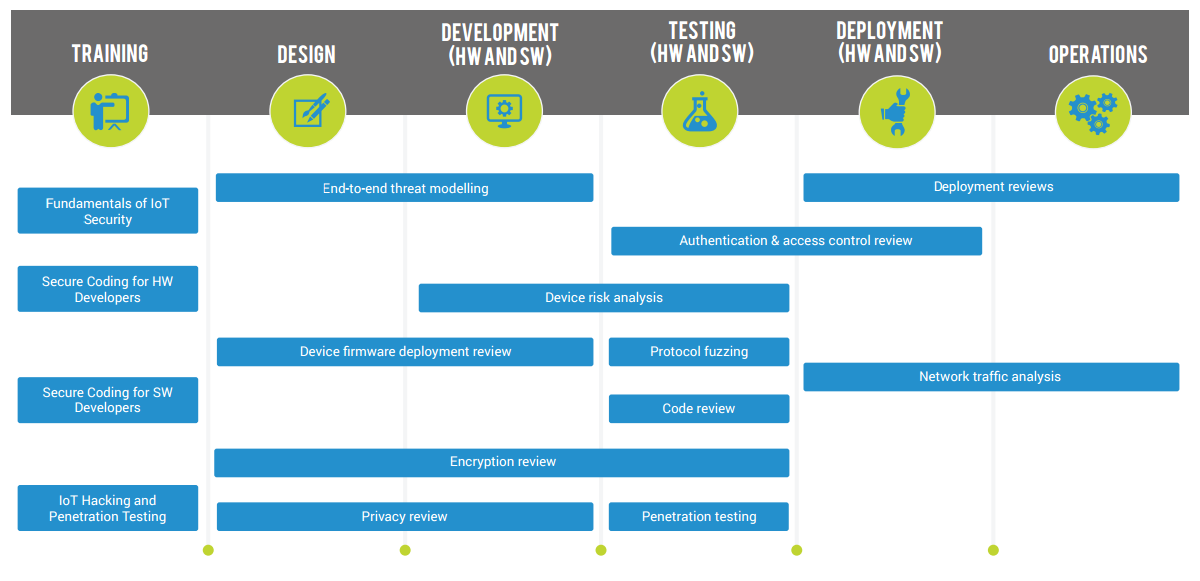
END-TO-END THREAT MODELLING
Threat modeling involves an in depth overview of product design in order to define potential threats to the system and develop a strategy to address and prevent vulnerabilities before they are created.
The objective of Threat Modeling is to methodologically analyze security aspects of the planned / designed system in order to:
- IDENTIFY potential threats and risks
- DEFINE required countermeasures
The most common and industry recommended methodologies used for threat modeling are: STRIDE and DREAD.
DEPLOYMENT REVIEWS
Formal review and analysis of plans throughout the design, development, and deployment stages of an IoT infrastructure.
The objective of the reviews is to define a path to maintaining optimal user and corporate privacy.
The Deployment review may include:
- SECURITY PROCESSES for provisioning devices and maintaining fleets.
- AUDIT LOGS & DEVICE CONFIGURATION -For existing products and platforms, businesses may evaluate audit logs and device configurations.
- OWNERSHIP STRATEGIES – A deployment review may include reviewing strategies for ownership of IoT devices.
- CLOUD SERVICES- Deployment reviews can be conducted on any cloud services or other gateways.
AUTHENTICATION AND ACCESS CONTROL REVIEW
The objective of the review is end-to-end analysis of authentication and access control processes used in an IoT eco system.
- OS ANALYSIS – analysis of a device’s operating system
- AUTHENTICATION SCHEME– review of authentication schemes used in the cloud or the device
- CERTIFICATE MANAGEMENT.
- PASSWORD POLICIES – review of existing password creation and change policies
DEVICE RISK ANALYSIS
IoT devices are designed and produced by a multitude of device manufacturers, who must comply with standards and regulations.
We provide an in depth analysis of device hardware and software in order to provide a deeper understanding of the attack surface and threats associated with the device.
The risk analysis process can also assist in identifying vulnerabilities and exploits associated with the device.
DEVICE FIRMWARE DEPLOYMENT REVIEW
During the lifetime of an IoT device, new bugs will be discovered and the firmware will need to be updated. A review of the firmware deployment and re-deployment strategy provides a clear evaluation of current strategy and closing the gaps regarding hardware updates.
PROTOCOL FUZZING
Communications between devices, gateways, and cloud services are performed via usage of a variety of protocols.
In order to minimize exploitation of protocol related vulnerabilities it is vital to standardize usage of protocols and manage protocol related risks.
NETWORK TRAFFIC ANALYSIS
Analyzing network topologies and traffic patterns is most important in order to identify and prevent network based vulnerabilities with a special emphasis on the communication matrix of an IoT product.
CODE REVIEW
Review of all code running on devices, gateways, and the cloud will reveal vulnerabilities created during software development or integration.
The output of a code review will be a detailed report of findings and recommendations for mitigation and best practices.
ENCRYPTION REVIEW
Comprehensive review of all encryption algorithms in use of all related devices and cloud in order to evaluate strength of eco system encryption and provide recommendations regarding preferred recommended encryption algorithms.
PENETRATION TESTING
Performance of a full eco system penetration test of the product will identify both risks of each component on its own, and risks related to the interface of components.
The output of a penetration test will be a detailed report of findings and recommendations for mitigation and best practices.
PRIVACY REVIEW
Evaluation of individual and organization privacy stature in relation to the IoT product.
Issues addressed:
- User information privacy
- Company information privacy
- IP Protection.





