More on training
As cyber crime is evolving in magnitude and impact, addressing security in your software development lifecycle is no longer “nice to have”, IT IS A MUST.
The Problem
Most talented developers do not have a clue how to integrate security throughout the development lifecycle.
What classically happens is that at the end of the development lifecycle right before the release stage, the security requirements are addressed and security testing is performed only to discover major vulnerabilities in the product/application which require adjustments in the application code and maybe even as far back as the application design.
The result is
- Time consuming mitigation phase
- High cost for reaching security approval
The Solution
Integrating security into your product from the get-go means we know exactly when we need to intervene and at what critical points security must be addressed.
Extra Info. List, links to related pages
What is SDLC and How Can We Help?
SDLC is a method developed to ensure security issues as well as compliance requirements are addressed throughout the development lifecycle in the most effective way.
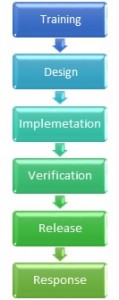
The classical SDLC includes addressing security from the requirements, design stage throughout the actual development and of course through the verification and release stages:
Training → Design → Implementation → Verification → Release → Response
AppSec Labs provides full support at all levels and stages of the development lifecycle in order to help our customers achieve the security they are striving for from their products.
Organizational SDLC
AppSec Labs will take your company one step ahead by assisting your company in securing not only a single or multiple development projects; we will help you create a methodology which will enforce correct implementation of security into company work methodology and bring your development processes to the maturity level you are seeking.
Activities carried out in the framework of the consulting services – promotion of organizational SDLC
System Mapping and Classification
Application mapping
- Creating a document describing the application.
- Determining priorities, based on the importance of the application.
- Case study – selecting representative systems for the purpose of analyzing main weak points and providing an overview of the organization’s application security level.
Mapping critical problems
- Locating main issues and common organization-wide development mistakes
- Architecture review
- Penetration test
- Code review
- Production of a document describing the main problems
- Providing guidelines for correcting these problems
Accompanying corrections of security issues
- Prioritizing
- Close guidance of correction process
- Answering questions during the process
Testing corrections made to the systems
- Testing the type of fixes performed, location of additional vulnerabilities (not defined critical) and regression checks
- Penetration test
- Code review
- Comments and retests until required state is reached
Methodologies
Guidance documents
- Secure development guideline document
- Creation of a list of requirements for designers / architects etc.
- Creation of a checklist for developers.
Secure development methodology
- Implementation of secure development methods into the organization’s existing methodology documents
- Improvement of existing procedures
- Definition of check points throughout the development process, in between the different phases.
Standardization
Defining organizational standards for development and use of network security mechanisms (software infrastructure)
- Authentication
- Authorization
- Input validation
- Log management
- Cryptography
- Deployment
- Data storages
Stabilizing Organizational Systems
Corrections in rest of systems
- Realizing corrections to problems found system-wide throughout the systems in the organization.
- Check of the corrections
Accompanying developments in new systems
- Secure development guidelines
- Consultation during planning phase and performance of design review
- Performing code review during writing of the code
- Penetration testing at the end of the development process
- Close accompaniment during security bug fixes process
New developments in previously tested systems (deltas)
- Testing of all the new developments made since the last test, and between corrections being made to the old code and the current code.
Building an Organizational Secure Development Infrastructure
Increasing the involvement of QA teams in the security testing process
- Targeted training for QA teams on performing penetration tests
- Creation of security test cases for the QA team
Determining organizational control points in the development process – approval of relevant party at critical points
- Design approval from a security point of view before moving on to writing of the code
- Code scan before moving to testing environment
- Penetration test before moving to production. SDLC-based development
Consulting for development projects
- Building a secure project management plan
- Training for the project manager
Project development control
- Attendance in the design meetings – performance of secure design review
- Sample code tests
- Meetings with development teams – review of code snippets in new modules on a permanent basis
- Unit security testing