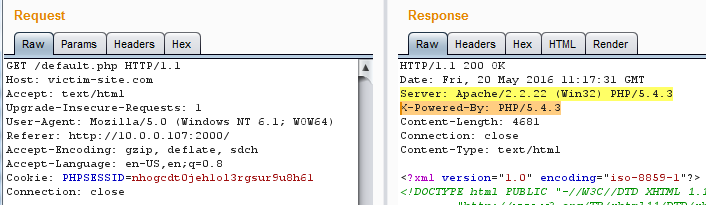
Disable Excessive headers – Apache
Methods
1. To remove the Server header, follow these steps:
- Load the hread module in the Apache httpd.conf file, by adding the following line:
LoadModule headers_module modules/mod_headers.so
- After headers_module is loaded, set the following lines in httpd.conf:
ServerTokens Prod ServerSignature Off
ServerSignature removes the version ifnp from the page generated by apache web server (e.g. 403, 404, 502, etc.)
ServerTokens changes Header to production only, i.e. Apache
- Restart apache service.
2. To remove X-Powered-By header, include following lines in the httpd.conf.
<IfModule mod_headers.c> Header unset X-Powered-By </IfModule>
3. For Apache Coyote, edit the server.xml configuration file found at: CATALINA_HOME/conf/server.xml
<Connector
port="8080"
...
server="Apache"
/>
4. For JBoss 6.0, JBoss 7.0, JBoss 7.1, modify the catalina.properties file located in: ${jboss.home}/server/${server.instance.name}/deploy/jbossweb.sar/.
Set the property org.apache.catalina.connector.X_POWERED_BY to false.
References
https://httpd.apache.org/docs/2.2/mod/core.html#serversignature
https://httpd.apache.org/docs/2.2/mod/mod_headers.html#header
http://docs.jboss.org/jbossweb/7.0.x/sysprops.html
https://tomcat.apache.org/tomcat-8.0-doc/security-howto.html
https://www.owasp.org/index.php/Securing_tomcat