Description
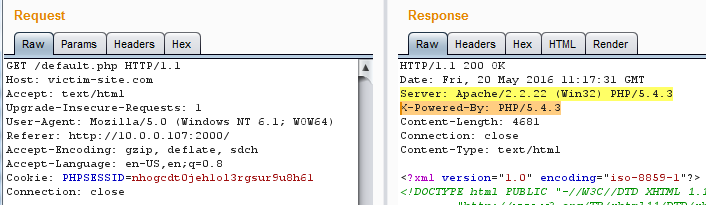
Different client technologies such as Web, Mobile Cloud and more – sends messages to business applications using XML. In order for the application to work with these self-descriptive XML messages, it has to parse them and check that the format is correct.
XML External Entity (XXE) attacks occurs when the attacker declares an external entity inside an XML message that is sent to the server, and uses it in the body of the XML message. When the XML parser receives the XML message, it notices the reference to the entity and looks for the value of the entity to replace the entity’s reference with the actual value.
External entity meant to be declared in an XML document, to reference external source to be fetched and be used as the content of the entity – this behavior leads to scenarios where the attacker can inject “SYSTEM” identifier which tells the XML parser that the value of the entity is actually a file path on the local server.
The result will allow the attacker to read files located on the application server such as “/etc/passwd” or “c:\windows\win.ini”
Same goes for Internal URLs in an organization – the attacker will be able to extract the content of these URLs using XXE attack assuming he has additional info about internal servers.
See how to fix it!
Read more →