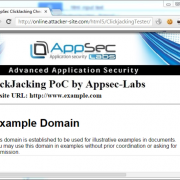
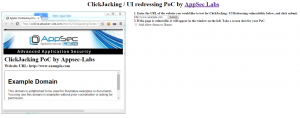
Android 5.x Application-Security-related updates
Hi
I just copied and summarized the security-related changed in Android 4.4, 5.0 and 5.1. Enjoy guys!
Custom permission
Android 5.0 prevents the installation of apps if they define a custom permission that is already defined by an existing resident app.
Web view
The WebView default behavior was changed to block mixed content. Please do not use: setMixedContentMode..
SSL default configuration
Android 5.0 introduces changes to the default TLS/SSL configuration used by apps for HTTPS and other TLS/SSL traffic:
- TLSv1.2 and TLSv1.1 protocols are now enabled
- AES-GCM (AEAD) cipher suites are now enabled
- MD5, 3DES, export, and static key ECDH cipher suites are now disabled
- Forward Secrecy cipher suites (ECDHE and DHE) are preferred