Online ClickJacking/UI redressing PoC Tester
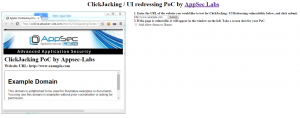
AppSec Labs is proud to introduce the ClickJacking Tester – a tool which is designed to allow information security specialists around the world to easily check online whether their websites are vulnerable to ClickJacking/UI redressing attack:
http://online.attacker-site.com/html5/ClickjackingTester/
How to Use:
- Open the tool in your browser.
- Enter your website’s URL in the text box.
- Check “add allow-forms to Iframe” box in order to add the ‘allow-forms in the sandbox’ attribute in case it is necessary.
- Hit ‘enter’ or click submit button.
- If the page is vulnerable, it will be displayed in the window on the left side of the testing page.
- Take a screenshot for your PoC and enjoy!
What is ClickJacking/UI Redressing?**
Clickjacking, also known as a “UI redress attack”, is when an attacker uses multiple transparent or opaque layers to trick a user into clicking on a button or link on another page when they were intending to click on the top level page. By doing this, the attacker effectively hijacks clicks meant for one page and routs them to another page, most likely owned by another application, domain, or both.
Using a similar technique, keystrokes can also be hijacked. With a carefully crafted combination of stylesheets, iframes and text boxes, users can be led to believe they are typing in the password to their email or bank account, but are instead typing into an invisible frame controlled by the attacker.
Examples
For example, imagine an attacker who builds a web site that has a button on it that says “click here to receive a free iPod”. However, on top of that web page, the attacker has loaded an iframe with your email account, and exactly lined up the “delete all messages” button directly on top of the “free iPod” button. The victim believes he is clicking on the “free iPod” button, but instead actually clicks on the invisible “delete all messages” button. In essence, the attacker has hijacked the user’s click, hence the name “ClickJacking”.
One of the most notorious examples of Clickjacking was an attack against the Adobe Flash plugin settings page. By loading this page into an invisible iFrame, an attacker tricked a user into altering the security settings of Flash, giving permission for any Flash animation to utilize the computer’s microphone and camera.
Clickjacking also made the news in the form of a Twitter worm. This clickjacking attack convinced users to click on a button which caused them to re-tweet the location of the malicious page, and propagated massively.
There have also been clickjacking attacks abusing Facebook’s “Like” functionality. Attackers can trick logged-in Facebook users to arbitrarily like fan pages, links, groups, etc.
Mitigation
There are two main ways to prevent clickjacking:
- Sending the proper X-Frame-Options HTTP response headers that instruct the browser to not allow framing from other domains.
- Employing defensive code in the UI to ensure that the current frame is the most top level window.
**For more information on Clickjacking and its mitigation, please see the Clickjacking Defense Cheat Sheet.



Leave a Reply
Want to join the discussion?Feel free to contribute!