Angular Template Injection without Quote Characters
Introduction
When you’re trying to detect XSS in an Angular application (AngularJS or Angular >2, the version doesn’t matter for this post), you’ll probably try the following possibilities:
- You enter a basic XSS payload such as <script>alert(0);</script>
- You find out that the developer encoded the output properly and the < > characters turn into < and >
- Your next attempt will be a client-side template injection: {{1338-1}}
- The application displays 1337
- From here on, it will be straight-forward: you’ll find a payload that matches the Angular version of the app and pop that alert to get a Proof of Concept.
However, in some cases, the output sanitation applies not only to characters like > and < but also encodes single and double quote characters ( ‘ will turn into ', etc.)
This means that if you try to insert a payload that has quotes in it, for example:
{{constructor.constructor('alert(0)')()}}
It will turn into
{{constructor.constructor('alert(0)')()}}
At this point, your expression will trigger a syntax error and the payload will fail.
So, what can we do about it?
When trying to avoid quotes in a payload (because it contains strings) the easiest way is to use functions that generates strings. In JavaScript, we will need to use the String object, specifically, the String.fromCharCode() method

The issue in this case (Angular applications) is that we cannot just call String.fromCharCode()in an Angular expression:
{{constructor.constructor(String.formCharCode(...))()}}

It will not work because Angular limits us to only using the properties and variables that are accessible under Angular’s scope. (More about the scope here: https://github.com/angular/angular.js/wiki/Understanding-Scopes). If Angular wasn’t stopping us from accessing objects outside the scope, we wouldn’t need to access the Stringobject. As attacker, we could just inject {{window.alert(0)}}
So what do we do when we don’t have access to the Stringobject but we still need to call fromCharCode() to generate our “alert(0)” string?
We can use this payload:
{{constructor.constructor(valueOf.name.constructor.fromCharCode(...))()}}

Let’s break it down
- We used valueOf.name because it returns a string value. Right now, it doesn’t matter what string is returned. As long as it’s a string variable – we’re good to go. In the same way, we could use any of the following possibilities as they all generate strings:

- Now that we have a string variable in our payload, let’s look at its constructor:

- The constructor itself is a String object! Now, all we have to do is to add a dot character and access all of the available functions in the String object including fromCharCode

By getting to the String object in this indirect way, even though the object itself isn’t in Angular’s scope, we can create an Angular, Client-Side Template Injection payload without needing single or double quotes

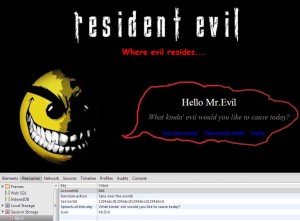
And here’s our alert 🙂 without quotes.
Acknowledgements
Big shout-out goes to the folks from PortSwigger and Tomer Haddad