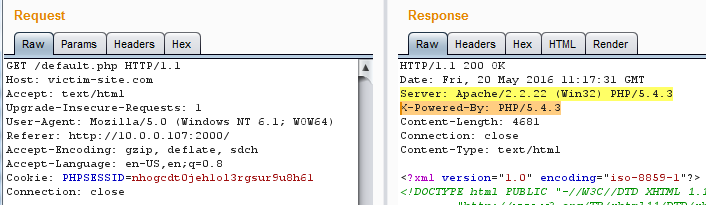
Disable Excessive headers – IIS
Methods
1. Remove the Server header by adding the following code to the Global.asax.cs file in your project:
protected void Application_PreSendRequestHeaders(object sender, EventArgs e)
{
Response.Headers.Remove("X-AspNet-Version");
Response.Headers.Set("Server","FooServer");
}
2. To remove the X-AspNet-Version header set the following, in the Web.config:
<configuration>
<system.web>
<httpRuntime enableVersionHeader="false" />
</system.web>
</configuration>
3. To remove X-AspNetMvc-Version, add the following line in the Application_Start event in Global.asax:
protected void Application_Start()
{
MvcHandler.DisableMvcResponseHeader = true;
}
4. To remove the X-Powered-By header set the following in the Web.config file:
<configuration>
<system.webServer>
<httpProtocol>
<customHeaders>
<remove name="X-Powered-By" />
</customHeaders>
</httpProtocol>
</system.webServer>
</configuration>
5. To suppress all the other headers ensure that the Web.config contains the following xml:
<configuration>
<nwebsec>
<httpHeaderModule>
<suppressVersionHttpHeaders enabled="true" />
<httpHeaderModule>
</nwebsec>
</configuration>
6. Alternatively, follow the following instructions of IIS configuration:
https://blogs.msdn.microsoft.com/varunm/2013/04/23/remove-unwanted-http-response-headers/