Resident XSS – Reflected Becomes Stored Thanks to HTML5
HTML5 is the newest version of the HTML. It offers new features that enhance support for creating web applications that can interact with the user and his/her local data and servers. HTML5 successfully does this more easily and effectively than has previously been possible.
In this article we will focus on the new client storage offered by HTML5. The new HTML provides us with the Local & Session Storage, which can hold 15MB and more of client data. The differences between them is that the Local Storage can be accessed from any window, while the Session Storage can by read/modified by the same window only. Additionally, the data within the Session Storage will be automatically deleted when the window is closed, whilst deletion of the data in the Local Storage must be done manually.
Let’s say that the web application stores your account number, the SessionId, username, and some other data that will be read later on in order to display the data without sending requests to the server. The website takes the data it previously entered to the storage and displays it when the page renders. This is how the page looks normally, along with the original information stored in the sessionStorage:
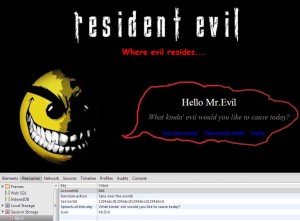 (Click on the image to enlarge)
(Click on the image to enlarge)
Notice that the message within the speech bubble takes its information from the Session Storage, as can be seen in the above image, right below the page. You can access the page’s Resources tab using Chrome’s Developer tools (a.k.a Inspect Element).
We can assume that the page’s code behind it looks something like this when retrieving the data from the Session Storage:
<script>
var username = window.sessionStorage.getItem(“username”);
var speech = window.sessionStorage.getItem(“Speech-of-the-day”);
var action = window.sessionStorage.getItem(“Random-action”);
</script>
If this website is vulnerable to a Reflected XSS (which in the regular case would be executed once on the response that includes it) and if the website does not perform client-side encoding (escaping), then this Reflected XSS can become a Stored XSS.