In recent years, Sony Pictures Entertainment has been one of the most highly targeted companies by cyber crime groups.
The last months of the year 2014 were very tough on Sony, after a cybercriminal group which identifies itself as GOP (Guardians of Peace) performed the biggest cyber-attack on Sony Pictures Entertainment. In this article I will make a short summary of the attack:
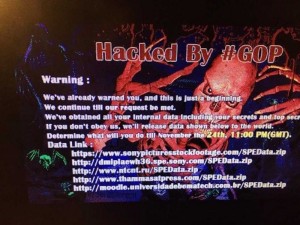
When Sony Pictures employees came into the office on Monday, November 24th 2014, they discovered that their corporate network had been hacked. The attackers had left messages threatening to release sensitive information if Sony didn’t comply with the attackers’ demands; All Sony employees found the same message on their computer screens (see the above picture)
The GOP hacker group claimed responsibility for the hack and had apparently stolen reams of internal corporate data as well. GOP leaked the movies Annie, Fury, Still Alice, Mr. Turner and To Write Love on Her Arms to the internet on Black Friday.
The massive data breach at Sony appeared to have exposed more sensitive documents, revealing the US Social Security Numbers of more than 47,000 celebrities as well as freelancers, current and former Sony employees. Employees at Sony Pictures Entertainment were sent a threatening email by the GOP. The e-mail was written in English and asked the company employees:
“Please sign your name to object the false (sic) of the company at the email address below, if you don’t want to suffer damage. If you don’t, not only you but your family will be in danger.”
A number of DDOS attacks (Distributed Denial-of-Service attack is an attempt to make a machine or network resource unavailable to its intended users) were launched against Sony servers by several hackers groups.
Read more →