Case study – Open Redirect
Most of us are familiar with the ‘Open Redirect’ vulnerability; an OWASP top 10 vulnerability that takes advantage of a situation in which the application receives a parameter from the client and uses it to build the URL location to which the user is redirected, without performing sufficient validation on the received input.
Typically, attackers can exploit vulnerable applications in order to perform phishing attacks, redirecting the victims to phishing sites that look exactly (or partially) like the vulnerable application. The victims tend to believe they are still in the original website, and provide their credentials in order to perform the required login. Unfortunately, these credentials are sent directly to the attacker.
A Classic Open Redirect Scenario
The following image demonstrates a vulnerable website (victim-site.com), which is vulnerable to the common open redirect scenario; a login page that will redirect the user to the page specified in the ‘returnURL’ parameter after successful login (the rectangle outlines the URL of the index page):



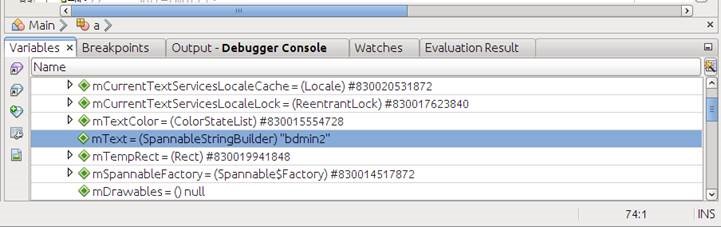



 Android is based on a customized Linux OS version. The main differentiation from the classic PC Linux is that the Android OS was adapted to define every Application on the device as a separate User or entity.
Android is based on a customized Linux OS version. The main differentiation from the classic PC Linux is that the Android OS was adapted to define every Application on the device as a separate User or entity.